Moving away from passwords with Windows 10, Windows Hello for Business & Microsoft Intune
In 2004, long before we went online massively concepts like phishing or ransomware were on the rise, Bill Gates, predicted at the RSA Conference that year the demise of passwords saying “they just don’t meet the challenge for anything you really want to secure.”
For years, we’ve been discussing the vulnerabilities of passwords (80 percent of security breaches are down to stolen passwords & credentials) and the need to ditch them for more robust & secure solutions. Many initiatives have been launched like Microsoft’s CardSpace, the Higgins project, the Liberty Alliance, NSTIC, the FIDO Alliance and various Identity 2.0 proposals. All with the explicit goal of eliminating passwords.
Password-less strategy
Over the past few years, Microsoft has continued their commitment to enabling a world without passwords. At Ignite 2017, Microsoft shared a four-step approach which helps organizations going password-less.
1. Develop a password replacement offering
2. Reduce user-visible password surface area
3. Transition into a password-less deployment
4. Eliminate passwords from the identity directory
Passwords aren’t working but still we massively relying on it
That’s not the only problem with passwords. Another challenge is their omnipresence. They’re so widely used to protect online accounts & services that the modern internet user has to memorize, on average, the passwords for up to 92 accounts. The inevitable result is password recycling, where users reuse passwords across multiple platforms. That means that if an attacker obtains a password for an unrelated account, they might inadvertently get their hands on a victim’s online bank account details or even worse.
Reduce user-visible password surface area
With Windows Hello for Business & passwords coexisting in your environment, the next step towards password-less is to reduce the password surface. The environment & workflows need to stop asking for passwords. The goal of this step is to achieve a state where the user knows they have a password, but they never use it. This state helps decondition users from providing a password any time a password prompt shows on their computer. This is how passwords are phished. Users who rarely, if at all, use their password are unlikely to provide it. Password prompts are no longer the norm. A way to achieve this goal is to reduce the password surface area by removing the Password Credential Provider.
Credential Providers
Credential providers are the primary mechanism for user authentication—they currently are the only method for users to prove their identity which is required for logon and other system authentication scenarios. With Windows 10 and the introduction of Windows Hello (former known as Microsoft Passport), credential providers are more important than ever; they will be used for authentication into apps, websites, and more in different ways.
Below illustration by Jairo Cadena provides a clear overview how credential provider is positioned on Windows 10 in both a Active Directory (hybrid) & Azure Active Directory (modern) environment.

Credential providers are registered on a Windows machine & are responsible for:
• Describing the credential information required for authentication.
• Handling the communication and logic with any external authentication authorities.
• Packaging the credentials for interactive and network logon.
Microsoft provides a variety of credential providers as part of Windows, such as password, PIN, smartcard, and Windows Hello (Fingerprint, Face, & Iris recognition). With the upcoming Windows 10 19H1 release the Sign-in option UI has received an update including support for the use of new sign-in capabilities such as security keys.

Please find below an overview of available Microsoft System Credential Providers.

The credential provider can be found in de following registry key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers
Stimulate Windows Hello for Business
As we’re focusing on reducing the password surface area we made the assumption your organization have a password replacement offering (e.g. 3rd party or Windows Hello for Business) already in-place. A first step in our approach is to disallow users from using there password to log in, by enforcing Windows Hello for Business.
We can use Group Policy to deploy an interactive logon security policy setting or using Microsoft Intune to configure this setting via PowerShell.
$registryPath = “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System”
$Name = “scforceoption”
$value = “1”
IF(!(Test-Path $registryPath))
{
New-Item -Path $registryPath -Force | Out-Null
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}
ELSE {
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}


Reduce user-visible password surface area
Another, more effective option is to remove the ability from users to log on by using passwords, by removing (disable) the password credentials provider at the Windows logon screen.
We can use Group Policy to exclude credential provider(s) administrative template logon setting or using Microsoft Intune to configure this setting via PowerShell.
$registryPath = “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}”
$Name = “Disabled”
$value = “1”
IF(!(Test-Path $registryPath))
{
New-Item -Path $registryPath -Force | Out-Null
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}
ELSE {
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}
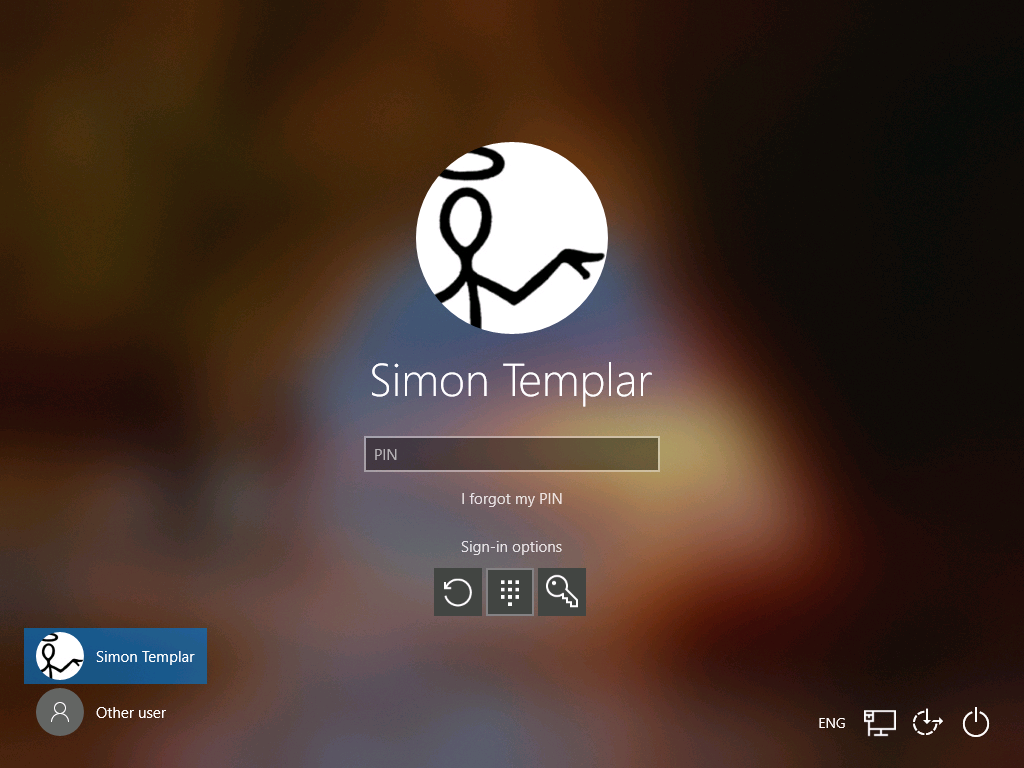
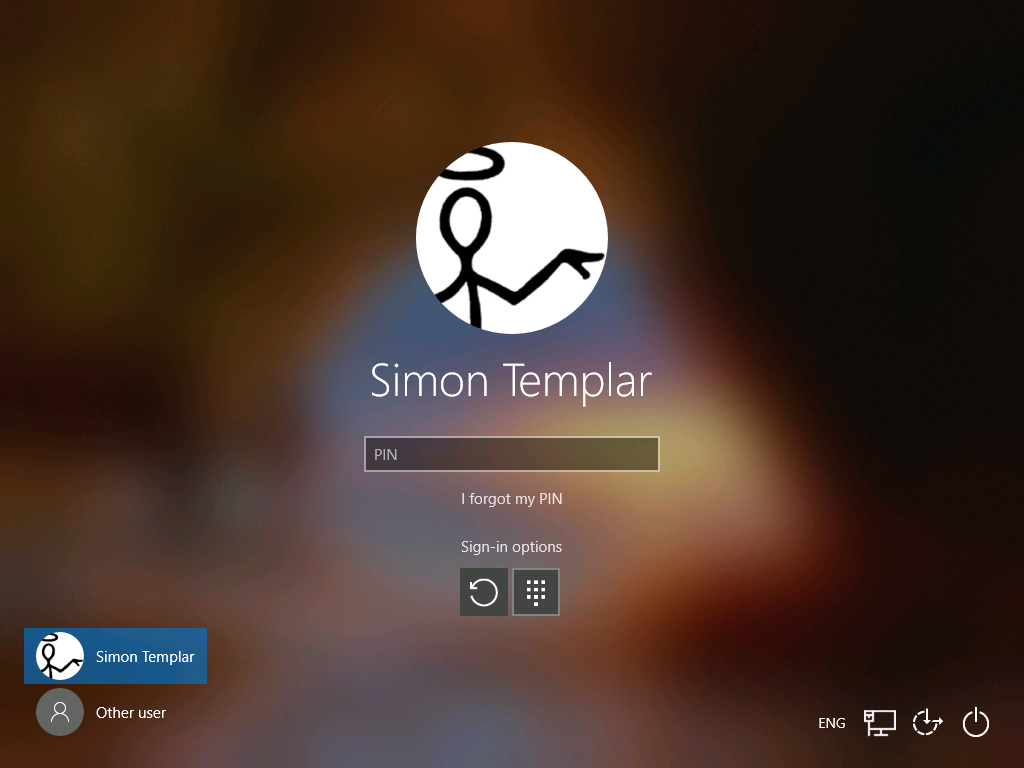
Transition into a password-less deployment
Windows Hello Multifactor Device Unlock provides multifactor device authentication for login or unlocking Windows 10 devices. Default, Windows, supports the use of a single credential (password, PIN, fingerprint, face, etc.) for login or unlocking your device. Therefore, if any of those credentials are compromised (shoulder surfed), an attacker could gain access to your local device only. Since Windows 10 (1709) Windows offers Multifactor device unlock by extending Windows Hello with trusted signals. You can configure Windows 10 to request a combination of factors and trusted signals to unlock your Windows 10 devices.
We can use Group Policy to exclude credential provider(s) administrative template logon setting or using Microsoft Intune to configure this setting via PassportForWork CSP Policy.
More detailed explanation on how to configure Windows Hello Multi-factor Device Unlock can be found in a previous blog post “Enable Windows 10 Multifactor Authentication with Windows Hello Multifactor Device Unlock & Microsoft Intune“


Microsoft Intune PowerShell Scripts
Promoting Windows Hello for Business is a good starter however we want to hit the next level and reduce the password surface area by removing the password credential provider. In a modern scenario Group Policies are out of scope whereby Administrative Templates (preview) and Policy CSP are limited to configure this specific setting Microsoft Intune. Using Microsoft Intune PowerShell scripts we’ve a fallback in order to achieve our goal.

Note: PowerShell scripts deployed via Microsoft (Intune Management Extensions) are by default executed in a 32-bit context on a 64-bit system which lead to unpredictable results. Highly valued community peers Oliver Kieselbach & Nickolaj Andersen created a wrapper to mitigate this behavior and allows you to run PowerShell scripts in 64-bit context.
Monitor your password-less journey
A great way to keep track of your password replacement adoption is Login Health (preview) solution of Windows Analytics (Azure Log Analytics). It provides a clear overview which login types being used, the usage and success rate. The figures below proves Windows Hello (Fingerprint, Face, & Iris recognition) are more convenient to your users giving the success rate.

Conclusion
In summary, there are multiple ways to enter a password-less area which provides a convenient and secure workplace. Bear in mind there is a reason why we’re still relying on passwords, so plan your password-less strategy carefully and enter this area step by step. Please invest some extra time for extensive testing and your patience will be rewarded.
A great read to define your password-less strategy is Microsoft Password-less Protection whitepaper which you can download here.
I want to discourage to the disable of all system credential providers or restrict your device compelling to ‘ford Knox’ standards. Keep in mind you’re responsible for a workplace which is loved by your users and trusted by IT. While extra device unlock factors may fulfill additional authentication requirements for particular groups of users, it is very important to ensure that the user can always regain access to their machine when a breaking change occurs.

With Intune Administrative Template (preview) Microsoft provides a way to change the logon experience, however the current feature set to configure the logon behavior is limited. The same applies to the Policy CSP, which enables you to configure 3 CredentialProviders policies on Windows 10 via Microsoft Intune or 3rd part MDM provider. An extension to this would be a more than a welcome addition to ease the implement of password-less.
Going password-less is a long-term approach for secure authentication, and it’s still evolving. It can take time to transition. For users that can’t go password-less, turn on MFA to validate users and minimize prompts based on the risk of the sign-in with conditional access capabilities.
No matter how big or small your ambitions are…think big, start small & move fast.
Sources
- https://github.com/SCConfigMgr/Intune/blob/master/Templates/Script-IntunePSTemplate.ps1
- https://github.com/okieselbach/Intune/blob/master/ManagementExtension-Samples/IntunePSTemplate.ps1
- https://jairocadena.com/2016/11/08/how-sso-works-in-windows-10-devices/
- https://docs.microsoft.com/en-us/windows/desktop/secauthn/credential-providers-in-windows
- https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/passwordless-strategy
- https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/feature-multifactor-unlock#configuring-unlock-factors
- https://en.wikipedia.org/wiki/Password
- https://cloudblogs.microsoft.com/microsoftsecure/2018/05/01/building-a-world-without-passwords/
- https://www.microsoft.com/en-us/cloud-platform/passwordless

One thought on “Moving away from passwords with Windows 10, Windows Hello for Business & Microsoft Intune” Leave a comment ›