Windows Defender ATP: Onboarding your Windows 10 endpoints, do it the right way!
In the early days of onboarding Windows 10 endpoints to Windows Defender ATP you had to define a custom device configuration policy via Intune, in order to enable and register your Windows Defender ATP agents at scale.
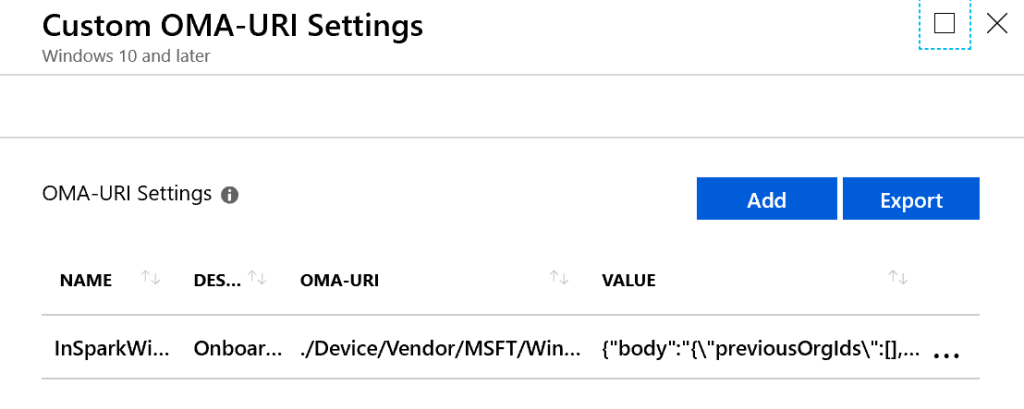
Later on the onboarding experience was improved by providing native Windows Defender ATP configuration policy via the Intune UI. It’s recommended to onboard your Windows 10 endpoints via the native configuration policy the more the fact Intune flags your Windows 10 endpoints as not configured/onboarded in the Windows Defender ATP connector status page.
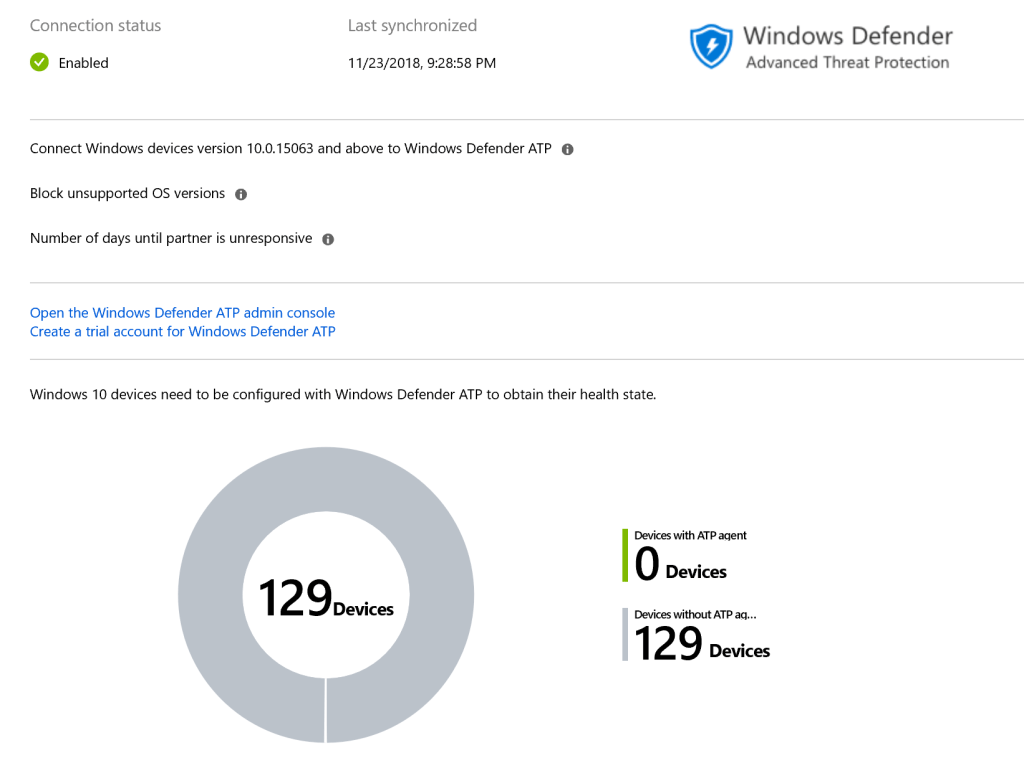
Intune makes you believe your Windows 10 endpoints were not onboarded to Windows Defender ATP, however this is not the case as we know they are however using the old onboarding approach.

Once revised the recommended approach of onboarding Windows Defender ATP endpoints, Intune starts reporting your Windows 10 endpoints as ‘healthy’ from an Windows Defender ATP onboarding perspective using the preferred onboarding approach.
ps. it can take a while in order to get the new device configuration being effectuated and reported back in Intune indicated your Windows 10 endpoints reported healthy.
Would be great if you specify which licence we need to use defender ATP.
For example, i use a M365 business licence, and ATP is NOT included…..