Revise your OneDrive (Sync) restrictions when shifting to a Modern Workplace!

What is a modern workplace these days without having your personal- or group data synced to OneDrive and taking the full advantage Microsoft’s cloud storage has to offer!? One of the most asked feature is silently configuring your OneDrive client to automatically synchronize your (personal) data.
Silent configuration
Over time the silent configuration of OneDrive for Business has been improved. In the early days we were designated using semi-automatic methods using registry keys and scripts by Per Larsen, old school group policies, or by custom OMA-URI policies to do the magic. Nowadays OneDrive can easily be configured using Administrative Templates (31 settings) via Microsoft Intune. (almost the same as GPO but wrapped in a modern UI called Microsoft Intune 😉)

Modern Workplace
Last week I was preparing a modern workplace demo fully automated and managed by cloud. This puts Windows Autopilot on the menu including automatic enrollment & management, encryption, policies, software deployment and…silently configuration of OneDrive for Business client.
Challenge
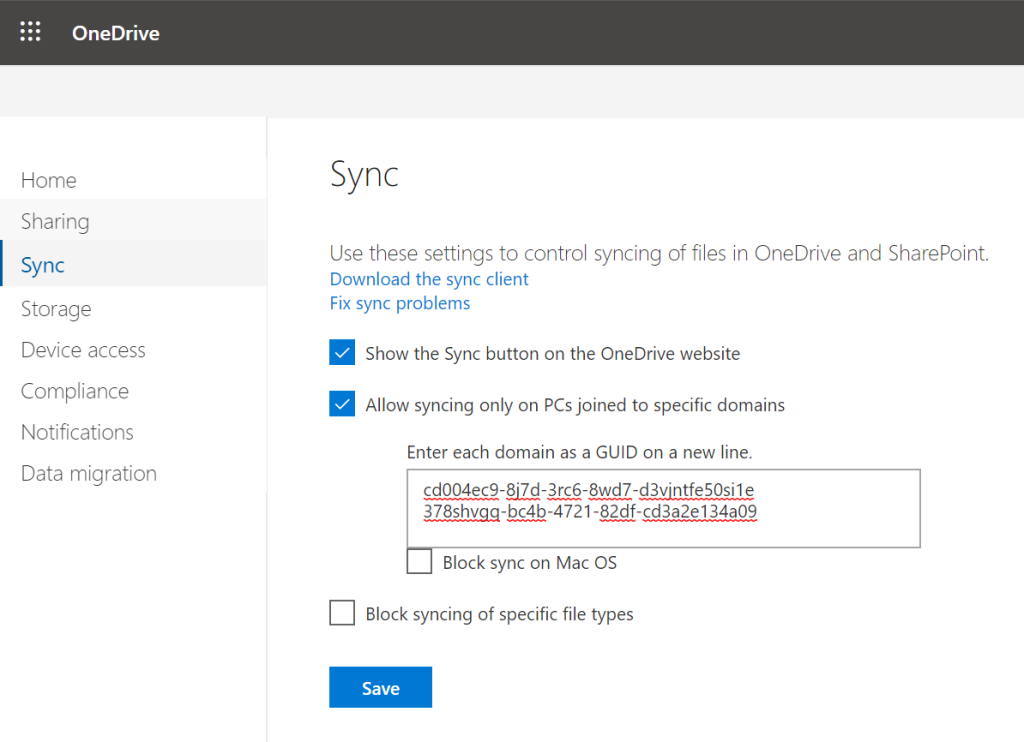
But what if silent configuration isn’t working as expected? This might become challenging where traditional and modern workplace comes together, you can end up in a situation where they do not fit. This will be the case when you’re preventing managed computers to sync OneDrive which are joined to a specific (Active Directory) domain(s).
It’s a no-brainer to opt-in for automatically (silently) configure the OneDrive for Business client. But in this case the OneDrive for Business client configuration was far from silent if you asked me! We ran into a challenge where OneDrive for Business client won’t be configured silently. Even when we tried to configure OneDrive sync manually, we didn’t succeed and ran into the following error “Sorry, OneDrive can’t add your folder right now“. So I reached out and contacted support 😉

Root cause
After some research I came across a blog of Chen Tian Ge who used Fiddler to take down a similar scenario. So after installed Fiddler myself, it was clear to me what caused the problem. I had found the undisputed proof. The reason for the failure is the fact the customer had implemented OneDrive sync client restrictions by using (AD) domain GUID. The modern workplace of course, did not meet the domain GUIDs requirement because it belongs to an Azure AD domain instead of AD joined domain.

Restrict OneDrive syncing to specific domains
This feature works fine for computers which are joined to an Active Directory (AD) domain, but causes challenges when shifting to a modern workplace joined to Azure Active Directory (Azure AD).
Conditional Access
The underlying reason for implementing these controls is to make sure companies remain control of where your corporate data is going through. Lastly, preventing from ending up at unmanaged or non-compliant devices. Allow syncing only on computers joined to specific domains works for AD joined devices but doesn’t fit for a (native) modern workplace which is Azure AD Joined.

Azure AD Conditional Access control capabilities in Azure AD offer simple ways for you to secure resources in the cloud. The OneDrive for Business client works with the Conditional Access control policies to ensure syncing is only done with managed and/or compliant devices. For example, you might require sync to be available only on domain-joined devices or devices that meet compliance as defined by Microsoft Intune.
Alongside Conditional Access, Microsoft Cloud App Security (MCAS) can be used to implement complementary data leak prevention (DLP) policies to make sure you stay in control no matter where your corporate data goes.
Get out of the old, get in with the new
Shifting from a traditional to a modern workplace isn’t just a matter of migrating the current, but a real transformation. Controls which worked well for many years in a traditional environment are often outdated by modern solution(s) that often work better and meet the revised needs/standards according a modern workplace.
Happy & safe syncing!
Sources
- https://docs.microsoft.com/en-us/onedrive/enable-conditional-access
- https://docs.microsoft.com/en-us/onedrive/allow-syncing-only-on-specific-domains
- https://docs.microsoft.com/en-us/intune/configuration/administrative-templates-windows
- https://docs.microsoft.com/en-us/cloud-app-security/data-protection-policies
- https://chentiangemalc.wordpress.com/2017/05/21/case-of-the-onedrive-for-business-sorry-cant-add-your-folder-right-now/
Categories
Hi,
Thank you for this very informative blog. I find that Mirosoft’s version is so vague.
I have a hybrid environment.
My question is, can i enable the Allow syncing only on computers joined to specific domains and then specify my AD local domain in there while simultaneously have implemented the Conditional Access Policy?
Just wondering if one cancels out the other.
Kind regards,
Andrew Maybir
Hi Andrew,
Thanks you for reading my blog! Yes, both technologies can coexist however Conditional Access is thè preferred and future proof solution direction. Important side note here is that your computers preferably should be Hybrid Azure AD Joined to apply device based Conditional Access (e.g. being managed and/or compliant).
Best regards,
Ronny de Jong
Hi Ronny,
Thank you for your reply. Oh great, i’ll go ahead and apply both methods. But i totally agree with you and using conditional access makes sense and this will be my next step once we have a plan to fully migrate our machines Azure AD Joined.
Do you have a link to a straight forward way to on how to add existing on-prem AD machines to Hybrid Azure AD?
Kind regards,
Andrew Maybir
You’re more than welcome! No, currently there are two options moving forward. Make your current AD machines Hybrid Azure AD or plan an in-place upgrade by Windows Autopilot.
Thank you Ronny,
Do you have a documentation on how to setup the Conditional Access for SharePoint and OneDrive to restrict syncing to unmanaged or personal laptops?
Kind regards,
Andrew
Hi, we face the need to allow share files externally from Onedrive, with some contacts in order to avoid the use of wetransfer or similar, but at the same time we aren’t comfortable with allowing everybody access from non corporate devices. We feel like we are going from 0 to 100 in terms of external access. So, I’m not sure what is the best practice here, but I imagine this scenario:
– External contacts added in the directory by IT can access remotelly from any device with pin code. –> this would allow them to access to the shared links from OneDrive, and may be limiting only download/read permissions should fit better.
– Internal users can only access onedrive from corporate devices.–> this reduces the risk of massive information exfiltration and allows us to “audit” the use of Onedrive from our SWG.
I mean, this is not perfect, since a user could provide a false external contact and share everything with it to exfiltrate, but at least we can see what is being shared/uploaded.
Thank you for your help!
Please start using Conditional Access to control Access for both external and internal users. This allows you to control the way users are able to access your assets (e.g. documents) whether from a Managed or unmanaged devices. This can also be used to allow internal users having a native experience on managed devices whether external users are only allowed to access them web based without the risk of exfiltration or data leaks. Ideally your are using External Identities (Guest Accounts) also known as B2B or B2C to provide them access to your directory (assuming Azure AD) without administrative overhead. Ice on the cake would be Identity Governance including Access Reviews to keep up whether guest user are still eligible to access your assets. OneDrive for Business can be used for direct sharing but ideally you’re using Teams to get the best user experience while keeping up being productive. Lastly Microsoft Cloud App Security (CASB) can be used to keep track of what’s being shared intentionally or whether you’re facing exfiltration of data leaks. Hope this help!
Hey thank you very much for your answer!
The problem is that external users do need to download files (we’re using it as a subtitute to wetransfer) and web-only mode won’t allow it. But one thing is that some people share some files with some external guests, and the other is to open completely the possibility of any internal user installing onedrive app in his personal pc or mobile and sync the files. The possibility of being accessed by a third party could be higher (mobile device lost, for example) in non corporative devices. I mean, it could seem contradictory to provide access to external users but not internal, but the amount of information leaked should be less in the case of external.
Thank you for your comments!