Part 2 – Deploy certificates to mobile devices using Microsoft Intune NDES – Connector
In part 1 of this blog series I provided some background and highlevel overview how the proces of deploying certificate profiles to devices works with Microsoft Intune.
- Part 1 – Deploy certificates to mobile devices using Microsoft Intune NDES – Overview
- Part 2 – Deploy certificates to mobile devices using Microsoft Intune NDES – Connector
- Part 3 – Deploy certificates to mobile devices using Microsoft Intune NDES – Deployment
- Part 4 – Deploy certificates to mobile devices using Microsoft Intune NDES – Troubleshooting
In this second blog – part 2 – I’ll outline the setup and configuration of the Microsoft Intune NDES connector. As starting point, we assume that you have already installed a Certificate Authorithy (CA), NDES server and an active Microsoft Intune subscription.
Prerequisites
Microsoft Intune NDES connector requires a number of (on-premise) infrastructure components. You are not able to use the Microsoft Intune NDES connector without these components. The following infrastructure components must be available whether on-premise or hosted in Azure (IaaS):
- Certification Server. A server running Windows Server 2012 R2 or Windows Server 2008 R2, set up as an Enterprise Certification Authority (CA). For instructions on how to set up a Certification Authority, see Install the Certification Authority. If you are using Windows Server 2008 R2, you need to install the following hotfix: http://support.microsoft.com/kb/2483564/.
- NDES Server. A server running Windows Server 2012 R2, set up to host the Network Device Enrollment Service (NDES). For instructions on how to configure Windows Server 2012 R2 to host NDES, see: Network Device Enrollment Service Guidance.
- Web Application Proxy Server (optional). A server running Windows Server 2012 R2, set up as a Web Application Proxy (WAP) server that will allow devices to receive certificates using an internet connection (recommended for security if devices will receive and renew certificates when connecting through the internet). The IIS SSL certificate will also need to be installed as a Trusted Root certificate for Android using Intune Policy, see Manage devices using configuration policies with Microsoft Intune. For instructions on how to configure Windows Server 2012 R2 to function as a WAP server, see: Working with Web Application Proxy. The December 2014 update rollup for Windows RT 8.1, Windows 8.1, and Windows Server 2012 will be required to enable the WAP server to handle the long URLs used by NDES.
Setup
The Microsoft Intune NDES connector can only be installed on a NDES server.
First you must enable you subscription to deploy certificates, which allows you to access certificate enrollment and revocation data. This is done by a simple click in the admin pane>mobile device management>Certificate Connector section.
Next step is to install the NDES Connector with administrative rights. The connector can be installed on a Windows member server.
Accept the EULA and provide a destination folder to install the NDES connector. Select a client authentication certificate which will be used for authenticating against Microsoft Intune and Microsoft Intune NDES Connector.
Select a client authentication certificate, and it needs to have the internal DNS name (FQDN) of the NDES server present in the Subject Alternative Name (SAN) of the certificate. It can be issued by customer PKI, a public PKI, or can be self-signed, but the NDES server needs to trust the issuer.
Note: The NDES server also needs an SSL (Server Authentication) certificate for https which will be used for client devices to reach it and make certificate requests. This certificate needs to have the publicly published DNS name of the NDES server in its Subject Alternative Name (SAN), and should be issued by either public CA or the customer’s corporate PKI. Intune will need to deploy the root CA certificate to clients to trust it if it is issued by the corporate PKI CA, so that clients can trust it. The two certificates can be combined into one, as long as that certificate contains both “Client Authentication” and “Server Authentication” EKUs, and as long as the SAN contains BOTH the internal DNS name AND the external DNS name in the SAN. (source provided & validated by Kevin Myrup, Microsoft)
Continue the setup…
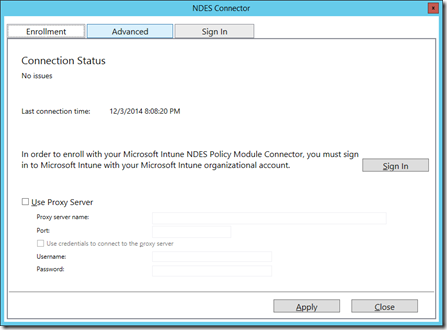
When completed the setup successfully check the option Launch Enrollment UI in order to register and associated your NDES connector to your Microsoft Intune subscription.
Now we have completed the setup on NDES server we need to configure the NDES connector and establish a connection between NDES connector and Microsoft Intune subscription. The NDES connector will forward the challange request to Microsoft Intune whether this challange is valid or not.
Make sure your NDES server have internet access (TCP 443) in order to succesfully complete the sign-in and registration process of the NDES connector.
Make sure you using an account which is global administator of your Microsoft Intune tenant.
When completed successfully you will prompted with the message-box Successfully enrolled.
A location to validate the installation on your NDES server is your Local Computer personal store which should looks as follows:
- <GUID> – This certificate is installed during the NDES connector is link to your Microsoft Intune subscritption. This certificate is used to encrypted the communication between NDES connector and Microsof Intune.
- <ndes.buildingclouds.lan> – This is the computer certificate of the NDES server including the FQDN subject name.
- NDES-MSCEP-RA – The encryption certificate will be used by the device to encrypt the password challenge it sends with the enrollment request.
- NDES-MSCEP-RA – The signing certificate will be used by the service to send the device request to the CA.
Your infrastructure is ready for the next phase, deploying certificate profiles to your devices. In part 3 of this blog series I’ll cover the deployment of certificates profiles uing the available policy templates in Microsoft Intune.
Categories









Hi this is very handy blog post. I am reading with a hope to kick off an implemention soon. One question, does the certificate above need to be a 3rd party certificate or can it be self signed?
Hi Dave, this can be both 3rd party (public issued) or self-signed certificate. In my case I used a self-signed certificate. have fun!
thanks for the reply.
hi sir
we are in process of Deploying the VPN profile through Intune by ndes server method, every certificate policy is deploying on the device but the VPN is not. do i need to have open internet in NDES server ? Does this mean we need to assign a public IP to our NDES server in order to make it available through internet ?
We are not using an WAP and right now NDES url is giving an error 403 which we should be getting according the Tech Net document we are following. ?
please reply!
What’s your exact issue, VPN profiles which are not coming down or the user certificates by NDES? By deploying the SCEP policy mobile devices are able to drop there SCEP requests to your NDES server which should be publicly accessible. You can publish NDES both through WAP or by Azure AD Application Proxy.
Regards,
Ronny
You should clarify that the certificate in your screenshot is the client authentication certificate, and it needs to have the internal dns name of the NDES server present in the Subject Alternative Name (SAN) of the certificate. It can be issued by customer PKI, a public PKI, or can be self-signed, but the NDES server needs to trust the issuer.
The NDES server also needs an SSL (Server Authentication) certificate for https which will be used for client devices to reach it and make certificate requests. This certificate needs to have the publicly published DNS name of the NDES server in its Subject Alternative Name (SAN), and should be issued by either public CA or the customer’s corporate PKI. Intune will need to deploy the root CA certificate to clients to trust it if it is issued by the corporate PKI CA, so that clients can trust it.
The two certificates can be combined into one, as long as that certificate contains both “Client Authentication” and “Server Authentication” EKUs, and as long as the SAN contains BOTH the internal DNS name AND the external DNS name in the SAN.